Class 12 Computer Science Sample Paper Set A
Please see below Class 12 Computer Science Sample Paper Set A with solutions. We have provided Class 12 Computer Science Sample Papers with solutions designed by Computer Science teachers for Class 12 based on the latest examination pattern issued by CBSE. We have provided the following sample paper for Class 12 Computer Science with answers. You will be able to understand the type of questions which can come in the upcoming exams.
CBSE Sample Paper for Class 12 Computer Science Set A
Section-I
Select the most appropriate option out of the options given for each question. Attempt any 15 questions from question no 1 to 21.
1. Find the invalid identifier from the following
(a) def
(b) For
(c)_bonus
(d)First_Name
Answer: A
2. Given the lists Lst=[‘C’,’O’,’M’,’P’,’U’,’T’,’E’,’R’] , write the output of: print(Lst[3:6])
Answer: PUT
3. Function of writer object is used to send data to csv file to store.
Answer: writerow()
4. What will be the output of following program:
a=’hello’ b=’virat’ for i in range(len(a)): print(a[i],b[i])
Answer: h v
e i
l r
l a
o t
5. Give Output:
colors=[“violet”, “indigo”, “blue”, “green”, “yellow”, “orange”, “red”]
del colors[4]
colors.remove(“blue”)
colors.pop(3)
print(colors)
Answer: [‘violet’, ‘indigo’, ‘green’, ‘red’]
6. Which statement is correct for dictionary?
(i) A dictionary is a ordered set of key:value pair
(ii) each of the keys within a dictionary must be unique
(iii) each of the values in the dictionary must be unique
(iv) values in the dictionary are immutable
Answer: (ii)
7. Identify the valid declaration of Rec: Rec=(1,‟Vikrant, 50000)
(i)List
(ii)Tuple
(iii)String
(iv)Dictionary
Answer: (ii)
8. Find and write the output of the following python code:
def myfunc (a):
a = a + 2
a = a * 2
return a
print(myfunc(2))
Answer: 8
9. Name the protocol that is used to transfer file from one computer to another.
Answer: FTP
10. Raj is a social worker, one day he noticed someone is writing insulting or demeaning
comments on his post. What kind of Cybercrime Raj is facing?
Answer: Raj is a social worker, one day he noticed someone is writing insulting or demeaning comments on his post. What kind of Cybercrime Raj is facing?
11. Which command is used to change the existing information of table?
Answer: UPDATE
12. Expand the term: RDBMS
Answer: Relational Database management System
13. Write an Aggregate function that is used in
Answer: Count (*)
14. For each attribute of a relation, there is a set of permitted values, called the of that attribute.
(a) Dictionaries
(b) Domain
(c) Directory
(d) Relation
Answer: B
15. Name the Transmission media which consists of an inner copper core and a second conducting outer sheath.
Answer: Co-axial
16. Identify the valid statement for list L=[1,2,”a”]:
(i) L.remove(“2”)
(ii) L.del(2)
(iii) del L[2]
(iv) del L[“a”]
Answer: (iii) del L[2]
17. Find and write the output of the following python code:
x = “Python”
print(x[ : :-1])
print(x)
Answer: nohtyP
Python
18. In SQL, write the query to display the list of databases stored in MySQL. 1
Answer: show databases
19. Write the expanded form of GPRS?
Answer: General Packet Radio Service (GPRS
20. Which is not a constraint in SQL?
(a) Unique
(b) Distinct
(c) Primary key
(d) check
Answer: B
21. Define Bandwidth? 1
Answer: a band of frequencies used for sending electronic signals
Section-II
Both the Case study based questions are compulsory. Attempt any 4 sub parts from each question. Each question carries 1 mark
22. Observe the following table and answer the question (a) to (e) (Any 04)
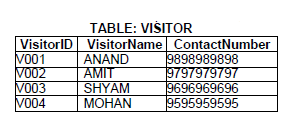
(a) Write the name of most appropriate columns which can be considered as Candidate keys?
(b) Out of selected candidate keys, which one will be the best to choose as Primary Key?
(c) What is the degree and cardinality of the table? 1
(d) Insert the following data into the attributes Visitor ID, Visitor Name and Contact Number respectively in the given table VISITOR.
Visitor ID = “V004”, Visitor Name= “VISHESH” and Contact Number= 9907607474
(e) Remove the table VISITOR from the database HOTEL. Which command will he used from the following:
a) DELETE FROM VISITOR;
b) DROP TABLE VISITOR;
c) DROP DATABASE HOTEL;
d) DELETE VISITOR FROM HOTEL;
Answer: (a) VIsitor ID and Contact Number 1
(b) Visitor ID 1
(c) Degree= 3
Cardinality=4
(d) insert into VISITOR values (“V004”, “VISHESH”,9907607474)
(b) DROP TABLE VISITOR;
23. Priti of class 12 is writing a program to create a CSV file “emp.csv”. She has written the following code to read the content of file emp.csv and display the employee record whose name begins from “S‟ also show no. of employee with first letter “S‟ out of total record. As a programmer, help her to successfully execute the given task.
Consider the following CSV file (emp.csv):
1,Peter,3500
2,Scott,4000
3,Harry,5000
4,Michael,2500
5,Sam,4200
import ________ # Line 1
def SNAMES():
with open(_________) as csvfile: # Line 2
myreader = csv._______(csvfile, delimiter=’,’) # Line 3
count_rec=0
count_s=0
for row in myreader:
if row[1][0].lower()==’s’:
print(row[0],’,’,row[1],’,’,row[2])
count_s+=1
count_rec+=1
print(“Number of ‘S’ names are “,count_s,”/”,count_rec)
(a) Name the module he should import in Line 1 1
(b) In which mode, Priti should open the file to print data. 1
(c) Fill in the blank in Line 2 to open the file. 1
(d) Fill in the blank in Line3 to read the data from a csv file. 1
(e) Write the output he will obtain while executing the above program. 1
Answer: (a) csv 1
(b) read mode 1
(c) ’emp.csv’ 1
(d) reader 1
(e) 2,Scott,4000
5,Sam,4200
Number of “S” names are 2/5
PART-B
Section-I
24. If given A=2,B=1,C=3, What will be the output of following expressions:
(i) print((A>B) and (B>C) or(C>A))
(ii) print(A**B**C)
Answer: (i) True
(ii) 2
25. What is Trojan? Any two type of activities performed by Trojan
OR
What is the difference between HTML and XML?
Answer: A Trojan horse or Trojan is a type of malware that is often disguised as legitimate software.
Trojans can be employed by cyber-thieves and hackers trying to gain access to users’systems. activities performed by Trojan can be:
Deleting data
Blocking data
Modifying data
Copying data
Disrupting the performance of computers or computer networks///25
OR
26. Expand the following terms:
(a) HTTP
(b) POP3
(c) VOIP
(d)TCP 2
Answer: a. HTTP-Hypertext transfer Protocol
b. POP3-Post office protocol ver. III
c. VOIP- Voice over internet Protocol
d. TCP- Transmission control protocol
27. What do you understand the default argument in function? Which function parameter must be given default argument if it is used? Give example of function header to illustrate default argument
OR
Ravi a python programmer is working on a project, for some requirement, he has to define a function with name CalculateInterest(), he defined it as:
def CalculateInterest (Principal, Rate=.06,Time): # code But this code is not working, Can you help Ravi to identify the error in the above function and what is the solution.
Answer: Default argument in function- value provided in the formal arguments in the definition header of a function is called as default argument in function. They should always be from right side
argument to the left in sequence. For example:
def func( a, b=2, c=5): # definition of function func( ) here b and c are default arguments
OR
In the function CalculateInterest (Principal, Rate=.06,Time) parameters should be default
parameters from right to left hence either Time should be provided with some default value or
default value of Rate should be removed
28. Rewrite the following Python program after removing all the syntactical errors (if any), underlining each correction:
def checkval:
x = input(“Enter a number”)
if x % 2 =0:
print (x, “is even”)
elseif x<0:
print (x, “should be positive”)
else;
print (x, “is odd”)
Answer: Rewrite the following Python program after removing all the syntactical errors (if any),
underlining each correction:
def checkval: # checkval( )
x = input(“Enter a number”) # int(input(“Enter a number”))
if x % 2 =0:
print (x, “is even”)
elseif x<0: # elif
print (x, “should be positive”)
else; # else:
print (x, “is odd”)
29. What possible outputs(s) are expected to be displayed on screen at the time of execution of the program from the following code? Also specify the maximum values that can be assigned to each of the variables FROM and TO.
import random
AR=[20,30,40,50,60,70]
FROM=random.randint(1,3)
TO=random.randint(2,4)
for K in range(FROM,TO):
print (AR[K],end=”#“)
(i)10#40#70#
(ii)30#40#50#
(iii)50#60#70#
(iv)40#50#70#
Answer: Maximum value of FROM = 3
Maximum value of TO = 4
(ii) 30#40#50#
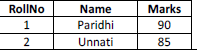
30. Define Primary Key of a relation in SQL. Give an Example using a dummy table.
Answer: Primary Key- one or more attribute of a relation used to uniquely identify each and every tuple in the relation. For Example : In the below Table Student, Roll No can be the Primary Key
31. Consider the following Python code is written to access the record of CODE passed to function: Complete the missing statements:
def Search(eno):
#Assume basic setup import, connection and cursor is created query=”select * from emp where empno=________”.format(eno)
mycursor.execute(query)
results = mycursor._________
print(results)
Answer: { } and fetchone()
32. Differentiate between DDL and DML with one Example each.
Answer: DDL- Data definition language. Consists of commands used to modify the metadata of a table. For Example- create table, alter table, drop table DML-Data manipulation language. Consist of commands used to modify the data of a table.
For Example- insert, delete, update
33. What will be the output of following program:
s=”welcome2kv”
n = len(s)
m=””
for i in range(0, n):
if (s[i] >= ‘a’ and s[i] <= ‘m’):
m = m +s[i].upper()
elif (s[i] >= ‘n’ and s[i] <= ‘z’):
m = m +s[i-1]
elif (s[i].isupper()):
m = m + s[i].lower()
else:
m = m +’#’
print(m)
Answer: vELCcME#Kk
34. Write code in Python to calculate and display the frequency of each item in a list.
Answer: L=[10,12,14,17,10,12,15,24,27,24]
L1=[ ]
L2=[ ]
for i in L:
if i not in L2:
c=L.count(i)
L1.append(c)
L2.append(i)
print(‘Item’,’\t\t’,’frequency’)
for i in range(len(L1)):
print(L2[i],’\t \t’, L1[i])
35. Write a function COUNT_AND( ) in Python to read the text file “STORY.TXT” and count the number of times “AND” occurs in the file. (include AND/and/And in the counting)
OR
Write a function DISPLAYWORDS( ) in python to display the count of words starting
with “t” or “T” in a text file ‘STORY.TXT’.
Answer: def COUNT_AND( ):
count=0
file=open(‘STORY.TXT’,’r’)
line = file.read()
word = line.split()
for w in word:
if w in [‘AND’,’and’,’And’]:
count=count+1
file.close()
print(count)
(½ Mark for opening the file)
(½ Mark for reading word)
(½ Mark for checking condition)
(½ Mark for printing word)
OR
def DISPLAYWORDS( ):
count=0
file=open(‘STORY.TXT’,’r’)
line = file.read()
word = line.split()
for w in word:
if w[0]==”T” or w[0]==”t”:
count=count+1
file.close()
print(count)
(½ Mark for opening the file)
(½ Mark for reading word)
(½ Mark for checking condition)
(½ Mark for printing word)
36. Write a output for SQL queries (i) to (iii), which are based on the table: SCHOOL and ADMIN given below:
TABLE: SCHOOL
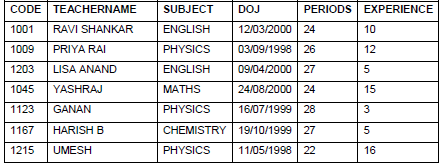
TABLE: ADMIN
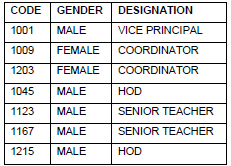
i) SELECT SUM (PERIODS), SUBJECT FROM SCHOOL GROUP BY SUBJECT;
ii) SELECT TEACHER NAME, GENDER FROM SCHOOL, ADMIN WHERE DESIGNATION = ‘COORDINATOR’ AND SCHOOL.CODE=ADMIN.CODE;
iii) SELECT COUNT (DISTINCT SUBJECT) FROM
Answer: i) ENGLISH 51
PHYSICS 76
MATHS 24
CHEMISTRY 27
ii) PRIYA RAI FEMALE
LISA ANAND FEMALE
iii) 4
37. Write a program to perform push operations on a Stack containing Student details as
given in the following definition of student node:
RNo integer
Name String
Age integer
def isEmpty(stk):
if stk == [ ]:
return True
else:
return False
def stk_push(stk, item):
# Write the code to push student details using stack.
OR
Write a program to perform pop operations on a Stack containing Student details as given in the following definition of student node:
RNo integer
Name String
Age integer
def isEmpty(stk):
if stk == [ ]:
return True
else:
return False
def stk_pop(stk):
# Write the code to pop a student using stack.
Answer: def stkpush(stk, item):
stk.append(item)
top=len(stk)-1
OR
def stkpop(stk):
if isEmpty( ):
print(“Underflow”)
else:
item=stk.pop( )
print(item)
if len(stk)==0:
top=None
else:
top=len(stk)-1
Section-III
38. PVS Computers decided to open a new office at Ernakulum, the office consist of Five Buildings and each contains number of computers. The details are shown below.
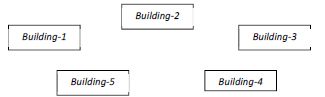
Distance between the buildings
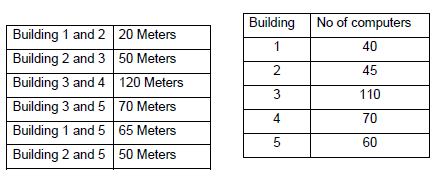
Computers in each building are networked but buildings are not networked so far. The Company has now decided to connect building also.
(i) Suggest a cable layout for connecting the buildings
(ii) Do you think anywhere Repeaters required in the campus? Why
(iii) The company wants to link this office to their head office at Delhi
(a) Which type of transmission medium is appropriate for such a link?
(b) What type of network would this connection result into?
(iv) Where server is to be installed? Why?
(v) Suggest the wired Transmission Media used to
Answer: (i) Any efficient layout with shortest Wire length
(ii) Between 3 and 4 due to larger distance
(iii) (a) Wireless
(b) WAN
(iv) Building-3 due to maximum no of Computers
(v) Co- axial cable or fiber optics
39. Write SQL queries for (i) to (v), which are based on the table: SCHOOL and ADMIN
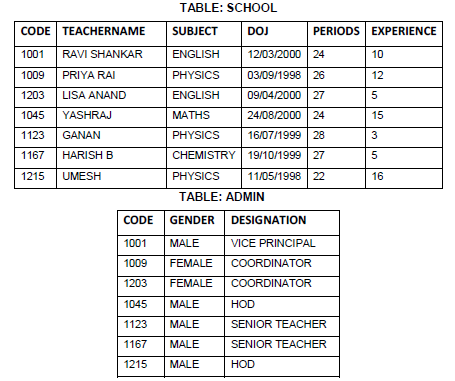
i) To decrease period by 10% of the teachers of English subject.
ii) To display TEACHER NAME, CODE and DESIGNATION from tables SCHOOL and
ADMIN whose gender is male.
iii) To Display number of teachers in each subject.
iv) To display details of all teachers who have joined the school after 01/01/1999 in
descending order of experience.
v) Delete all the entries of those teachers whose experience is less than 10 years in
SCHOOL table.
Answer: i) update SCHOOL set PERIODS=0.9*PERIODS;
ii) select SCHOOL. TEACHER NAME, SCHOOL.CODE, ADMIN.DESIGNATION from
SCHOOL, ADMIN where gender=’MALE’.
iii) select SUBJECT, count(*) from SCHOOL group by SUBJECT;
iv) select * from SCHOOL where DOJ>’ 01/01/1999’ order by EXPERIENCE desc;
v) delete from SCHOOL where EXPERIENCE<10;
40. Write a function S COUNT( ) to read the content of binary file “NAMES.DAT‟ and display number of records (each name occupies 20 bytes in file ) where name begins from “S‟ in it.
For. e.g. if the content of file is:
SACHIN
AMIT
AMAN
SUSHIL
DEEPAK
HARI SHANKER
Function should display
Total Names beginning from “S” are 2
OR
Consider the following CSV file (emp.csv):
Sl,name,salary
1,Peter,3500
2,Scott,4000
3,Harry,5000
4,Michael,2500
5,Sam,4200
Write Python function DISPEMP( ) to read the content of file emp.csv and display only
those records where salary is 4000 or above
Answer: def SCOUNT( ):
s=’ ‘
count=0
with open(‘Names.dat’, ‘rb’) as f:
while(s):
s = f.read(20)
s=s.decode( )
if len(s)!=0:
if s[0].lower()==’s’:
count+=1
print(‘Total names beginning from “S” are ‘,count)
OR
import csv
def DISPEMP():
with open(’emp.csv’) as csvfile:
myreader = csv.reader(csvfile,delimiter=’,’)
print(“%10s”%”EMPNO”,”%20s”%”EMP NAME”,”%10s”%”SALARY”)
for row in myreader:
if int(row[2])>4000:
print(“%10s”%row[0],”%20s”%row[1],”%10s”%row[2])
5
